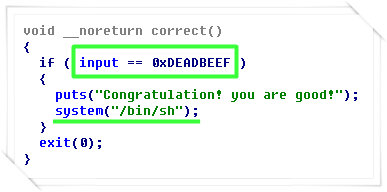
To comply with the write-up rule of pwnable.kr, I will talk about hints to solve this challenge. Here is no solution and correct answer. I ask for your understanding.
It is a challenge to read the flag by executing "fix". A source file called "fix.c" is provided. When I executed the "fix", I received two questions and got a "Segmentation fault" error.
<fix.c>
The vulnerable function "strcpy" is used and a buffer overflow occurs as expected. This results in an abnormal flow after the "shellcode()" function is terminated.
You can see what the shellcode looks like with the assembly code with the URL given in the source code, but I personally recommend using the "asm()" and "disasm()" functions in "pwntools" library. With this, shellcode index is added to each command line. It is also possible to know the corresponding machine code by entering commands without checking the opcode.
If you check with a debugger line by line, you can see that an error is occur in the middle of the shellcode. This error is caused by the ambiguous location of esp. That is, you need to change the location of esp to the proper place. In the case of me, I resized the stack with the "ulimit" command to avoid errors when changing the location of esp.
You can think of int 0x80 as a command to jump to the value in eax. And It is good to see how arguments are passed.
Then, the flag can be acquired.
It is a challenge to read the flag by executing "fix". A source file called "fix.c" is provided. When I executed the "fix", I received two questions and got a "Segmentation fault" error.
<fix.c>
#include <stdio.h>
// 23byte shellcode from http://shell-storm.org/shellcode/files/shellcode-827.php
char sc[] = "\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69"
"\x6e\x89\xe3\x50\x53\x89\xe1\xb0\x0b\xcd\x80";
void shellcode(){
// a buffer we are about to exploit!
char buf[20];
// prepare shellcode on executable stack!
strcpy(buf, sc);
// overwrite return address!
*(int*)(buf+32) = buf;
printf("get shell\n");
}
int main(){
printf("What the hell is wrong with my shellcode??????\n");
printf("I just copied and pasted it from shell-storm.org :(\n");
printf("Can you fix it for me?\n");
unsigned int index=0;
printf("Tell me the byte index to be fixed : ");
scanf("%d", &index);
fflush(stdin);
if(index > 22) return 0;
int fix=0;
printf("Tell me the value to be patched : ");
scanf("%d", &fix);
// patching my shellcode
sc[index] = fix;
// this should work..
shellcode();
return 0;
}
// 23byte shellcode from http://shell-storm.org/shellcode/files/shellcode-827.php
char sc[] = "\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69"
"\x6e\x89\xe3\x50\x53\x89\xe1\xb0\x0b\xcd\x80";
void shellcode(){
// a buffer we are about to exploit!
char buf[20];
// prepare shellcode on executable stack!
strcpy(buf, sc);
// overwrite return address!
*(int*)(buf+32) = buf;
printf("get shell\n");
}
int main(){
printf("What the hell is wrong with my shellcode??????\n");
printf("I just copied and pasted it from shell-storm.org :(\n");
printf("Can you fix it for me?\n");
unsigned int index=0;
printf("Tell me the byte index to be fixed : ");
scanf("%d", &index);
fflush(stdin);
if(index > 22) return 0;
int fix=0;
printf("Tell me the value to be patched : ");
scanf("%d", &fix);
// patching my shellcode
sc[index] = fix;
// this should work..
shellcode();
return 0;
}
The vulnerable function "strcpy" is used and a buffer overflow occurs as expected. This results in an abnormal flow after the "shellcode()" function is terminated.
You can see what the shellcode looks like with the assembly code with the URL given in the source code, but I personally recommend using the "asm()" and "disasm()" functions in "pwntools" library. With this, shellcode index is added to each command line. It is also possible to know the corresponding machine code by entering commands without checking the opcode.
If you check with a debugger line by line, you can see that an error is occur in the middle of the shellcode. This error is caused by the ambiguous location of esp. That is, you need to change the location of esp to the proper place. In the case of me, I resized the stack with the "ulimit" command to avoid errors when changing the location of esp.
You can think of int 0x80 as a command to jump to the value in eax. And It is good to see how arguments are passed.
Then, the flag can be acquired.