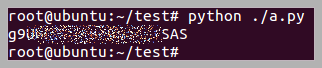
This is a quiz to find flags in web server logs.
The web server log contains the base64 encoding value in the order variable, and the URL encoding value in the end. Decode the URL encoding value, decode the Base64 value of the order variable, so the DB query is displayed.
❑ ASC : Ascending sort.
❑ case 1 when 1 then TRUE : Conditional statement(If-then-else)
❑ ascii() : char(ASCII code) → int
❑ char() : int → char(ASCII code)
❑ bin() : int → binary value
❑ substring(string, start, length) : This extracts a substring from a string.
❑ concat(exp1, exp2, exp3) : This returns concatenated expressions.
❑ field(value, val1, val2, val3 ) : This returns the position of the "value" in the list of values(val1, val2, val3).
[Query interpretation]
1. In the memvers table, extract the leftmost 1 character of the password value of the account that id is 1.
2. Convert the type of the extracted value(char → int → bin).
3. Extract the leftmost two values of the converted value and connect them.
4. If the connected value is 00, the server responds immediately, otherwise it responds late(2 or 4 or 6 seconds).
The time of the log differs by the sleep() time. That is, the attacker checked the password each bit with the server's reaction time.
■■ Logs corresponds to one password. The fourth log length is short because it extracts only one bit. When 7 bits are gathered, it becomes one ASCII code.
f = open("log.txt", "r")
sec = []
secRst = -1
secStr = ""
cvtStr = ""
rstStr = ""
while True:
aLine = f.readline()
if aLine == "":
break;
sec.append(int(aLine.split(" ")[3].split(":")[-1]))
for i in range(0,len(sec)):
if i == len(sec)-1:
break
secRst = sec[i+1]-sec[i]
if secRst < 0:
secRst+=60
if (i%4 == 0):
secStr = secStr + "\n"
secStr = secStr + str(secRst)
secStr = secStr.split("\n")
for k in range(1, len(secStr)):
for i in range(0,3):
if secStr[k][i] == "0":
cvtStr = cvtStr + "00"
elif secStr[k][i] == "2":
cvtStr = cvtStr + "01"
elif secStr[k][i] == "4":
cvtStr = cvtStr + "10"
elif secStr[k][i] == "6":
cvtStr = cvtStr + "11"
if k != len(secStr)-1:
if ■■■■■■■■■■■■■■
cvtStr = cvtStr + "0"
elif ■■■■■■■■■■■■■
cvtStr = cvtStr + "1"
cvtStr = cvtStr + "\n"
cvtStr = cvtStr.split("\n")
for i in range(0, len(cvtStr)):
rstStr = rstStr + chr(int(cvtStr[i],2))
print rstStr
f.close()
This is Python code to extract the flag value.The response time for the last attack log was unknown but did not affect the flag.